Aunque el uso de aplicaciones infectadas con malware para robar información financiera no es algo nuevo, los últimos hallazgos de la empresa rusa de antivirus Doctor Web apuntan a una escalada significativa, ya que los atacantes están atacando directamente la cadena de suministro de varios fabricantes chinos para cargar aplicaciones maliciosas en dispositivos completamente nuevos.
https://thehackernews.com/2025/04/chinese-android-phones-shipped-with.html
#Ciberseguridad #Seguridad #Privacidad #Aplicaciones #Malware
Recent searches
Search options
#malware
A Warning about Malicious PoCs:
cannot believe it is occurring to people that #DOGE IS NOT ABOUT EFFICIENCY BUT #SURVEILLANCE. just like #creditCards #Paypal #Uber #Tesla #Doordash #Amazon #Netflix #GMail #Instagram and every fin/techbro business.
the apartheid clown’s #malware is a ruse to give techbros the power to spy on all Americans.
these are the consequences of your silence while many of your friends & relations vilified us for saying, DEFUND THE POLICE. we didn’t just mean PDs. we meant the whole police state.
Microsoft Warns of Node.js Abuse for Malware Delivery – Source: www.securityweek.com https://ciso2ciso.com/microsoft-warns-of-node-js-abuse-for-malware-delivery-source-www-securityweek-com/ #rssfeedpostgeneratorecho #CyberSecurityNews #Malware&Threats #securityweekcom #securityweek #Malware #Nodejs

Threat actors misuse Node.js to deliver malware and other malicious payloads
Since October 2024, threat actors have been leveraging Node.js to deliver malware and payloads for information theft and data exfiltration. A recent malvertising campaign uses cryptocurrency trading themes to lure users into downloading malicious installers. The attack chain includes initial access, persistence, defense evasion, data collection, and payload delivery. The malware gathers system information, sets up scheduled tasks, and uses PowerShell for various malicious activities. Another emerging technique involves inline JavaScript execution through Node.js. Recommendations include educating users, monitoring Node.js execution, enforcing PowerShell logging, and implementing endpoint protection.
Pulse ID: 67fec5ac1e94a608250d9aa2
Pulse Link: https://otx.alienvault.com/pulse/67fec5ac1e94a608250d9aa2
Pulse Author: AlienVault
Created: 2025-04-15 20:46:36
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

Newly Registered Domains Distributing SpyNote Malware
Cybercriminals are employing deceptive websites on newly registered domains to distribute AndroidOS SpyNote malware. These sites imitate the Google Chrome install page on the Google Play Store, tricking users into downloading SpyNote, a powerful Android remote access trojan. SpyNote is used for surveillance, data exfiltration, and remote control of infected devices. The investigation uncovered multiple domains, IP addresses, and APK files associated with this campaign. The malware utilizes various C2 endpoints for communication and data exfiltration, with functions designed to retrieve and manipulate device information, contacts, SMS, and applications.
Pulse ID: 67feb504b76dd387be73309b
Pulse Link: https://otx.alienvault.com/pulse/67feb504b76dd387be73309b
Pulse Author: AlienVault
Created: 2025-04-15 19:35:32
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

Port of Seattle says ransomware breach impacts 90,000 people
Port of Seattle, the U.S. government agency overseeing Seattle's seaport and airport, is notifying roughly 90,000 individuals of a data breach after their personal information was stolen in an August 2024 ransomware attack.
#Seattle #PortOfSeattle #databreach #ransomware #malware #security #cybersecurity #infosec #hackers #hacking #hacked
As 'AI' coding 'assistants' invent nonexistent software libraries to download and use, enterprising attackers create and upload libraries with those names—laced with malware https://www.theregister.com/2025/04/12/ai_code_suggestions_sabotage_supply_chain
PasivRobber Malware Emerges, Targeting macOS to Steal Data From Systems and Apps
https://gbhackers.com/pasivrobber-malware-emerges-targeting-macos-to-steal-data/

ResolverRAT is distributed through phishing emails claiming to be legal or copyright violations tailored to languages that match the target's country.
New ResolverRAT malware targets pharma and healthcare orgs worldwide https://www.bleepingcomputer.com/news/security/new-resolverrat-malware-targets-pharma-and-healthcare-orgs-worldwide/
Slopsquatting
As AI coding assistants invent nonexistent software libraries to download and use, enterprising attackers create and upload libraries with those names&... https://www.schneier.com/blog/archives/2025/04/slopsquatting.html
We’re seeing an increasing volume of blocked queries to the SocGholish-related domain - blackshelter[.]org in the last several days.
New #threat: the evolving #Lummastealer evades detection using #base64 and #iplogger, abusing legitimate services for #malware distribution. Time to step up your #cyberresilience.
The Pall Mall Pact and why it matters | Malwarebytes | …I don’t entirely agree that this is a good thing
https://alecmuffett.com/article/113190
#HackingTools #PallMallPact #PallMallProcess #malware

Es gibt nichts zu sehen, bitte gehen Sie weiter. #microsoft #keylogger #malware
https://www.europesays.com/1997221/ NATO allies boost cyber defense coordination, focus on improving critical infrastructure resilience #CriticalInfrastructure #CriticalInfrastructureResilience #CyberDefense #CyberThreat #Cybersecurity #Europa #europe #InfrastructureResilience #MaliciousCyber #malware #nato #OTAN #ThreatIntelligence
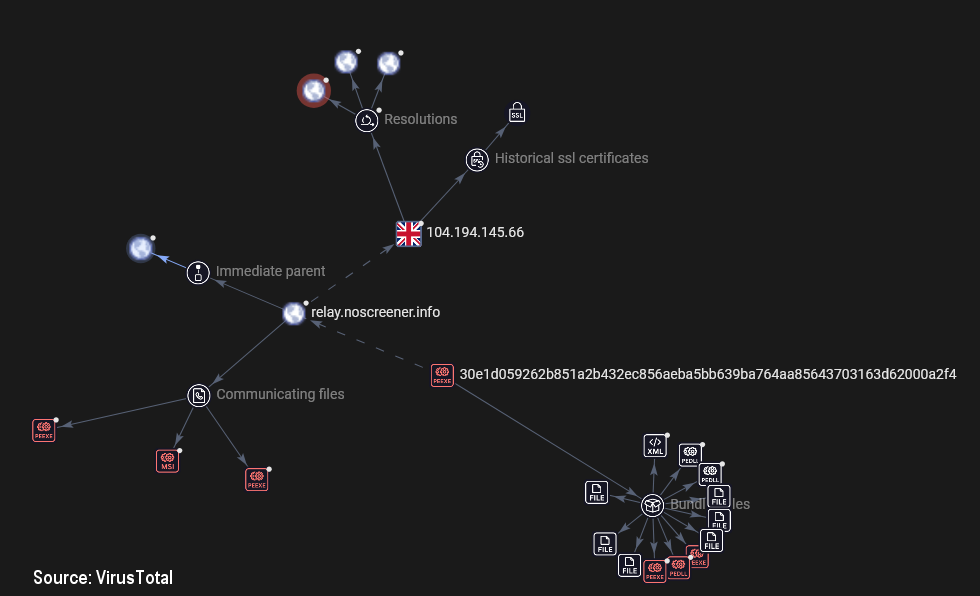
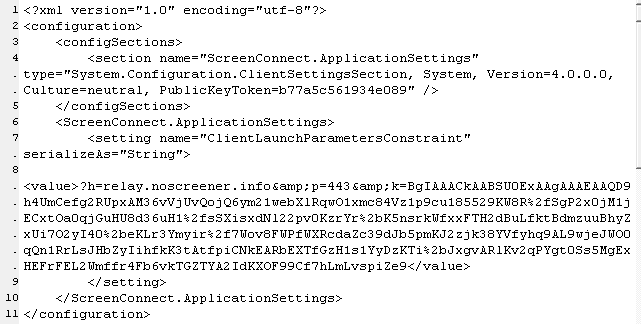
Last week I posted a thread about a #spam campaign delivering a #ConnectWise client as its payload. As of this morning, the threat actors have changed the payload (https://www.virustotal.com/gui/file/30e1d059262b851a2b432ec856aeba5bb639ba764aa85643703163d62000a2f4) and it appears to try to connect to the address "relay.noscreener[.]info" which resolves to 104.194.145.66.
Embedded in the installer .msi file is a file called system.config, which contains this domain name and a base64-encoded string.
The fake Social Security website is still being hosted on a compromised site that belongs to a temp agency based on the east coast of the US.
Previous thread:



![Graph depicting increased volume of blocked DNS queries to the SocGholish domain blackshelter[.]org in past several days. Graph depicting increased volume of blocked DNS queries to the SocGholish domain blackshelter[.]org in past several days.](https://sfo3.digitaloceanspaces.com/veganism-space/cache/media_attachments/files/114/342/733/141/345/689/original/f3069434f234256f.png)