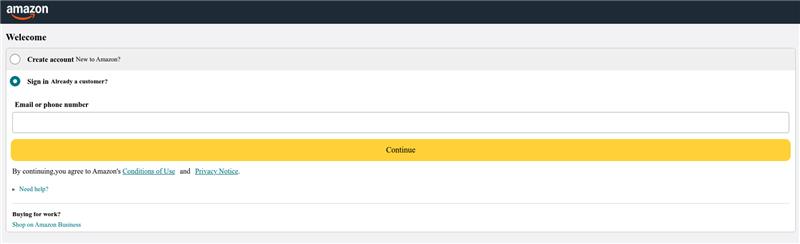
One of our researchers recently received a text from an unknown number saying they were eligible to receive a full refund for an Amazon order. The message contained a link to a URL on t[.]co, Twitter/X's link shortener. Clicking the link led to the domain 267536[.]cc, which hosted an Amazon phishing page.
From this lead, we were able to find many more domains hosting the same content. The actor registering the domains seems to like .cc, the country code TLD for the Cocos Islands.
Sample of the domains:
236564[.]cc
267536[.]cc
671624[.]cc
687127[.]cc
319632[.]cc